Introduction: What is the Five Eyes alliance?
The Five Eyes is an intelligence gathering and sharing alliance made up of five countries being Australia, United Kingdom, United States of America, New Zealand, and Canada. These countries pool the intelligence they gather, share resources, and vow not to spy against each other (this last point is debatable of course). This alliance has stood the test of time thanks to close strategic ties coupled with cultural similarities between the member countries. It continues to operate today monitoring state, private, and commercial communications worldwide through a range of means and programs outlined later. The terminology is shorthand for the intelligence releasability caveat: ‘AUS/CAN/NZ/UK/US EYES ONLY’.
History
Below is a brief history of the Five Eyes however our focus at Privacy Rightfully is to help you protect your privacy and security so the following has been left intentionally short and general in nature. If you are interested in greater details about the alliance there is plenty of information to be found online.
The alliance first formed in 1946 between the UK and USA, followed by Canada in 1948 with Australia & New Zealand becoming equal members of the alliance in 1956. The Five Eyes alliance has had a hand to play in many (probably close to all) notable conflicts over the past 74 years. For example, during the Vietnam War the US was supported by Australian and New Zealand operators stationed in the pacific region. British agents based in Hong Kong (a British colony at the time) also reported on North Vietnamese air defence networks. More recently, UN Weapons Inspector Hands Blix allegedly had his communications monitored by the Five Eyes leading into the Iraq War. It’s also claimed that Kofi Annan, the former UN Security-General, also had his office bugged by British agents.
There is a current and ongoing controversy that came to light as part of the Snowden revelations in 2013. This controversy is related to the accusation that Five Eyes countries are intentionally spying on one another’s citizens and then sharing that collected data with each other. This means each of the member countries can in a way ‘subcontract’ their dirty work to a partner country to keep their hands clean from any accusation of directly spying on their own citizens. Countries use such secret intelligence sharing arrangements to circumvent international and domestic rules on direct domestic surveillance.
The Five Eyes collaborate with other like-minded or strategically aligned countries such as Israel, Singapore, South Korea, Germany, France and Japan. Collaborations which include some of those countries listed above tend to be against threats of a geopolitical nature regarding traditional enemies such as Russia, China and North Korea. An agreement exists with the Five Eyes countries plus Denmark, France, Norway and the Netherlands known as the ‘Nine Eyes’. According to the Snowden revelations a working agreement exists with the Nine Eyes plus Belgium, Germany, Italy, Spain and Sweden known as the ‘Fourteen Eyes’.
How the Five Eyes gather information
Some of the proven and suspected ways the Five Eyes gather data include are listed below, follow the links for more details:
- ECHELON: A global network of radio antennae and satellites intercepting private and commercial communications (phone calls, faxes, emails etc). Intercepted data is sifted through by algorithms searching for keywords and red flags.
- PRISM program: Gathers user information from mainstream technology companies such as Google, Apple and Microsoft.
- ‘Upstream Collection’ programs: Gather data from the infrastructure data flows through such as fibre cables, switches and other parts of the internet backbone.
- TURBINE: a program that infects malware into devices allowing extraction of data from an infected device, recording of audio from the device microphone, taking snapshots using the device camera, corrupting files on the device, and exfiltrating data from USB drives connected to the device
- Mastering the Internet (MTI): A British mass surveillance project aimed at copying signals from fibre-optic cables at physical points of entry into Great Britain
- Hacking telecommunications companies
- Forcing companies to hand over their customer data via government orders
- Threatening or lobbying politicians and technology companies to pass laws undermining encryption standards and for service providers to create backdoors to encryption.
A full list of known government mass surveillance programs can be found here
The Five Eyes fight against encryption standards
If you’ve read our article Encryption 101 you will be aware of the strength modern encryption standards have to secure communication and information. The standards are so strong that true end-to-end encryption has the ability to keep the sophisticated powers of the Five Eyes from accessing encrypted content. Not happy that there is a security measure they cannot easily bypass they have over the years lobbied for provider companies to create backdoors to encryption standards to allow access for law enforcement. The FBI vs Apple case is a great example, where the courts ordered Apple to access the mobile phone recovered form a terrorist shooter (they didn’t). The Five Eyes doubled down on this lobbying at the end of 2018 when the law enforcement officials of Five Eyes issued a Statement of Principles on Access to Evidence and Encryption and again in 2020.
The pushback by privacy advocates is as you would expect however the issue of security is also at play and arguably more so than the issue of privacy. Cybersecurity experts and even the former FBI General Counsel argue, rightfully, that such backdoors or deliberate weakening of encryption standards will create a target for exploitation. Building in backdoors undermines the core of what makes encryption so powerful and secure in the first place and has far reaching cybersecurity consequences beyond the national security and crime fighting argument posed by the Five Eyes. Consider the quote below from a leaked National Security Council draft paper:
“Overall, the benefits to privacy, civil liberties, and cybersecurity gained from encryption outweigh the broader risks that would have been created by weakening encryption.”
The position against encryption weakening isn’t just from privacy advocates and cybersecurity experts but the business community more broadly. Businesses rely on the power of encryption to secure their systems, communications and intellectual property with any weakening of encryption standards creating a potential vulnerability and risk to their business. Nation-state espionage is increasingly targeting business communications which, thanks to the mobile era, tends to occur on personal devices. Uncompromised encryption protects more good than bad it would be argued and there is evidence of this from within the Five Eyes alliance itself. The lobbying to weaken encryption standards with backdoors for law enforcement, such as the 2018 statement linked earlier is signed by law enforcement officials of the Five Eyes countries. Curiously, it wasn’t signed by any heads or ministers of the various intelligence agencies of the Five Eyes indicating the branches within the Five Eyes most aware of the dangers of such backdoors and the importance of strong encryption to their work didn’t immediately add their name in support.
What can I do to protect my data?
Protecting or securing your data and privacy from the might of a near 75-year-old intelligence alliance is a big task. Indeed, governments and heads of state of countries that are friends and allies of the Five Eyes are targeted by their surveillance programs themselves! Furthermore given the parameters for intelligence sharing among the Five Eyes are classified there is limited public knowledge on the full spy power and capability the Five Eyes have access to including to cutting edge technology we don’t even know about yet. However, that doesn’t mean acquiescence is the sentiment you should have.
Jurisdiction:
With every digital service provider you use (such as Email, Password Manager, VPN, etc) it would be safe to assume if their servers or place of business are based in a Fourteen Eyes country then your data is at greatest risk of being accessed and shared between the intelligence agencies of those countries. Indeed, this is why you normally find the best rated privacy first providers tend to be in countries such as Switzerland (like ProtonMail) and Panama (like Nord VPN) amongst others. When choosing a digital service provider check where their servers are based as well as their business address and discount them in your selection process if either fall in a Fourteen Eyes country.
An additional consideration regarding jurisdiction, as we wrote in VPN 101, is knowing if your privacy focused providers are legal or accessible if you travel to different countries. VPNs are a great example as they’re not legal in all countries, whilst other countries such as China and its ‘Great Firewall’, may not let you access ProtonMail or your chosen VPN (for example). Considerations for jurisdiction are therefore threefold:
- Avoid providers based in or having servers in Fourteen Eyes Countries
- Look into the surveillance practises of those countries left
- Look into the surveillance practises and digital privacy laws and rights regarding countries you intend to travel to
Beyond jurisdiction:
Our natural tendency at Privacy Rightfully is to write our content with bad actors in mind – those with malicious intent targeting you specifically. They may be looking to gain from attacking your business, your personal life, your finances, your reputation, your sensitive data and so forth. This is quite different to the Five Eyes who see you as just another cog in their intelligence gathering projects in the name of national interests / national security. The Five Eyes, unlike bad actors, aren’t pooling their resources to do you harm assuming you’re not implicated as part of a government investigation (major tax fraud for example). However, the issue of course is that your communications or activities aren’t as secure or private as you may believe.
Therefore beyond using privacy first tools and service providers operating outside of Fourteen Eyes countries the next best thing to do is to continue taking precautions that make your private data harder to see and/or harder to link back to you (as you do against bad actors). This includes:
- Communication: Using end-to-end encrypted communication services such as we’ve listed at the end of our Encryption 101 article (Signal, Wickr etc)
- Browsing: Use a VPN when browsing, choose one outside of the Fourteen Eyes countries and with a strict ‘no logs’ policy
- Search: Use a privacy first search engine such as StartPage. Non Fourteen Eyes options include Swisscows and Searx
- Limit your device interconnectivity to minimise the links back to you, read IOT 101 for more information
- Use a reputable antimalware provider to ensure your devices aren’t bugged with spyware
What we’re saying is the precautions we’ve written about above and in the past to protect you against bad actors specifically will also serve you against government surveillance activities generally but to varying extents. Of course, beyond encryption, we can’t say with absolute confidence to what extent some of those points listed above do help. Some may and some may not (at all) because we don’t know exactly the cutting-edge technology the Five Eyes has access to now or into the future.
Our, perhaps surprising, position on Five Eyes surveillance
There is an issue with what a lot of privacy advocates are fighting for regarding more transparency about the treaties, programs, and agreements that underpin the Five Eyes surveillance activities. The issue of course is that such disclosures would weaken the legitimate work of the alliance, the gathering of intelligence that honestly and genuinely serve national security interests and identifies or prevents attacks by adversaries. The secretive nature of what the Five Eyes do and have the power to do is a necessary enabler of their effectiveness and success (funnily enough the same goes for encryption). Surprisingly perhaps, we’re not necessarily advocating for the Five Eyes to publicly share the details of their various surveillance programs and developments.
The Five Eyes alliance no doubt crosses moral and ethical boundaries regarding its means of intelligence gathering through the spying and surveillance that it does. We find ourselves in a juxtaposition in that we criticise these methods when they can breach our ideals of personal privacy yet praise our intelligence agencies when the same methods prevent a negative outcome or otherwise benefit national security. This is not to say we should give them a free pass, it’s just not so black and white and many of our colleagues in the privacy advocacy community are right in premise but not in practicality.
We at Privacy Rightfully are expected to stand firmly against any weakening of individual rights to privacy and the security of their data and other assets, which we do. However, we sympathise with the argument the Five Eyes puts forth in that the tools (such as encryption) you use to your advantage, are the same tools used by illegal operatives, criminals, and adversaries. Simplistically illustrated:
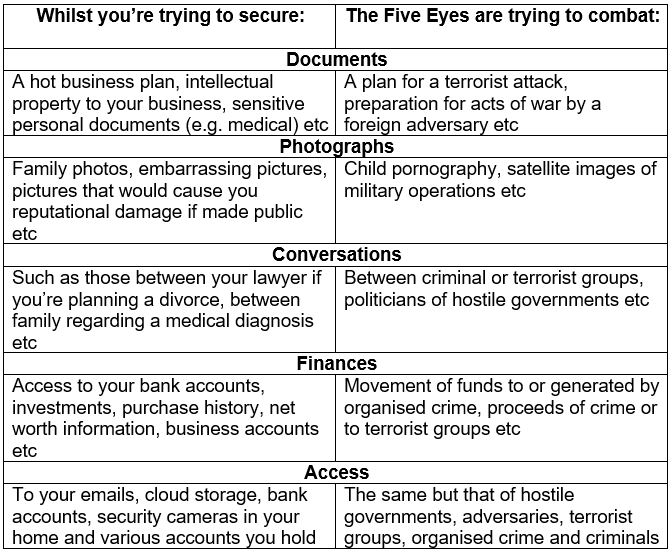
Herein is the issue, most people would advocate for your rights in the left-hand column whilst also supporting national intelligence agencies targeting of the right-hand column. The tools used by both sides of the table are the same though.
Whilst we don’t immediately advocate for alliances such as the Five Eyes be more open and transparent about their methods we do advocate against their weakening of privacy and security tools (such as creating backdoors to encryption standards). The reason they propose changes in laws, such to weaken encryption standards, is to make their jobs easier not that they will necessarily be better at their job (an important distinction). We’ve seen so many examples of government-imposed intrusion to our privacy, such as The Patriot Act or COVID-19 contact tracing that have netted results far below expectation and far below a fair return on the privacy concessions citizens have had to make.
The world has changed where communication and data storage is concerned and the strategies the intelligence community relies upon need to change with it. Foreign adversaries, terrorists, hostile governments, organised crime and the such have been around since well before the Five Eyes even formed. State intelligence agencies have been fighting them for centuries – they’re not new threats, only the tools they employ are new. Intelligence agencies need to be truer to their name and find ways to operate, successfully, without constantly turning to weakening of our (the general public) privacy options. It almost feels like a white flag, a concession, every time we’re asked to lose a little more control over our privacy – as if they have no other options.
Secrecy and confidentiality are necessary keys to the operation of intelligence services sure; we don’t advocate for them to tell us what they do and how they do it as most of the privacy advocacy community does. We take the position that intelligence agencies should get on with what they do whilst we as ordinary citizens will take our own precautions to secure ourselves and our data against bad actors first and against government surveillance as a by-product of that. We would say to the Five Eyes: ‘don’t come after or otherwise weaken the tools we have access to, such as encryption. We know you spy on us through your various programs, we won’t tell you not to (because it would fall on deaf ears anyway) and we want you to catch the bad guys, but we will take precautions and overall responsibility to make it harder for you to spy on us directly where we can‘.
We are of course against mass government surveillance principally, however, our fight isn’t lobbying governments or protesting against it as a first means of action as many of our colleagues do. Our fight takes the form of educating our readers how to establish their own systems to secure their data specifically and their privacy more generally. The government is difficult to stop, they’ll pass what they want and if they don’t, they’ll do as they wish behind the closed doors with their intelligence partners and, most of the time, we won’t ever find out (much of what you’re reading about today is public only thanks to the Snowden revelations for example).
Since we can’t ‘beat them’ the next best thing is to make sure they can’t get their five, nine, or fourteen eyes on our data by using tools such as encryption. The way we see it there is no clear winning position to take without dozens of caveats or concessions, on the one hand you have concepts, rights, and laws associated with privacy and security. On the other hand, you have the enabling of our intelligence agencies to keep us safe while we sleep, protect our industries and businesses from cybercrime, and the various national security arguments they cite as defence for their work.
We are against mass government surveillance but pragmatic enough to understand the need intelligence agencies have for surveillance. We are thankful for the Snowden revelations, for example, because they have brought the technological capabilities governments have for surveillance to light and shocked a lot of people to take action to protect their privacy and security. To put our views into one paragraph we’d say:
Intelligence agencies and their alliances are not the enemy here, the way we have been conditioned to indulge our personal lives and sensitive information to technology is at the heart of the surveillance problem. Our options are to either go offline or to take precautions with privacy first tools to establish our own systems and habits to maximise our security and privacy. You have the option to do the first and we’re working on helping with the second.
Conclusion
As discussed the threat of the Five Eyes seeing your data isn’t in the same league as that of a bad actor especially if, like most of our readers, you’re just an ordinary, law abiding citizen who is ahead of the curve when it comes to privacy consciousness. The point of today’s piece was to highlight there are more eyes looking for your data than just that of bad actors.
State intelligence agencies are likely a hundred times more sophisticated than the average hacker, employ the brightest experts in their fields, and likely have access to technology we don’t even know about (and thus we can’t suggest guaranteed countermeasures). Whilst it’s a bit mundane to finish with ‘do the best you can and employ as much of what we write about’ no one can promise a way to keep intelligence agencies, such as the Five Eyes alliance, at bay.
This article is written in line with our Terms & Conditions and Disclaimer. As such all content is of a general nature only and is not intended as legal, financial, social or professional advice of any sort. Actions, decisions, investments or changes to device settings or personal behaviour as a result of this content is at the users own risk. Privacy Rightfully makes no guarantees of the accuracy, results or outcomes of the content and does not represent the content to be a full and complete solution to any issue discussed. Privacy Rightfully will not be held liable for any actions taken by a user/s as a result of this content. Please consider your own circumstances, conduct further research, assess all risks and engage professional advice where possible.

