Introduction
Our previous article Understanding the deep and dark parts of the internet discussed how illegal products, services, and media can be sold online. This leads nicely into outlining what it is that bad actors want, what are they motivated by, and how they make money from their various attacks and breaches.
There are few articles in our library that don’t highlight precautions to take to protect against what you’re about to read in this article. Fundamentally, this article seeks to answer the question ‘what exactly is the threat that I’m protecting myself from by enacting what Privacy Rightfully writes about?’
To answer that question with a complete picture we have a lot to cover so be warned this is one of our longer articles! We’ve put key points or actions in bold font and utilised lists and tables to help present information as succinctly as possible. We didn’t break this down into separate articles as we wanted it to be read start to finish in the one sitting to keep the flow going.
The article contains the following five distinct parts with a conclusion at the end:
- The motivations of bad actors
- The types of data targeted by bad actors
- The methods typically used by bad actors
- The consequences of their success
- The precautions you can take
Part one
The motivations of bad actors
What do we mean by ‘bad actor’?
At Privacy Rightfully we refer to anyone as a ‘bad actor’ if they are taking actions that are likely to cause you harm. The term is broad and so its definition can change depending on the context and subject matter. For example, when we write about real world privacy and security issues we may refer to someone who scopes or assess your house for a potential burglary as a ‘bad actor’. Online we may refer to someone who simply doesn’t like you and will post embarrassing photos or commentary of you on social media or forums to damage your credibility or reputation as a ‘bad actor’. This article is mostly focused on the online world and a lot of what happens is as a result of some form of hacking. We’ll start by distinguishing the different types of hackers first, before using that to hone in on how we’ll define the term ‘bad actor’ for the purposes of this article.
Traditionally there have been three types of hackers:
- Black-hat hackers: These are the bad guys trying to find weaknesses in a security protocol to access a system, data, or content for a malicious purpose. They are usually experienced, intentional, and do a good amount of research on their targets
- White-hat hackers: They use their skills to help improve security by exposing vulnerabilities to businesses before these vulnerabilities become known to black-hat hackers. They are similar in skill to black-hat hackers and are typically employed as cybersecurity experts allowing them to use their skills for good. They can be hired but are also known to do what they do without expectation of payment, they are also known as ‘ethical hackers’
- Grey-hat hackers: Skew the lines between the two to various extents but typically break the law or ethical standards (as a black-hat) in their work but without the malicious intent (as a white-hat). For example, when they find a vulnerability, they’ll inform the owner of the system but without enough details for the owner to fix it. They may request a small fee (usually not a high value ransom) to fix the problem.
Recently three other types of hackers have been defined:
- Green-hat hackers: Novice hackers who are still learning and are unaware of the damage their actions can cause. They typically don’t have the knowledge or experience to fix any damage they’ve caused which is usually unintentional
- Blue-hat hackers: Seek revenge against a specific person, employer, business, or government institution. They typically do this for the purposes of doxing or damaging the reputation of a former partner or employer as they feel their target wronged them
- Red-hat hackers: Target black-hat hackers however employ the same unethical or illegal methods they do. Their motivation is considered noble, but their methods are not, for red-hatters it’s about fighting fire with fire.
For the purposes of this article when we refer to a ‘bad actor’ it is in most cases a black-hat hacker with the blue and green also at play in some situations and examples.
Motivations not based on financial gain
The following list includes situations where you may be the target either directly or indirectly (as collateral damage). With these there is typically no or limited financial gain for the bad actor and any financial gain isn’t the primary motivation for the attack, instead primary motivation tends to be:
- Revenge against a current or former employer or business by damaging their reputation or business value
- Revenge against you directly or personally, you may have wronged someone (or they’ve perceived it that way) recently or in your past such as an ex-partner or former employee. You may have gotten in a heated debate with someone online or posted support for a position which doesn’t align with them. The other in these scenarios could be a capable bad actor or someone with the resources and drive to hire one, usually this will go as far as complete doxing
- Hactivism which refers to targets that do not align with a bad actors political, ethical, religious, social, environmental or other views or positions. This tends to be ‘acts of protest’ striving to achieve a certain agenda, social change, legal change, or raising awareness through any subsequent media attention
- Espionage (business) to gain a level of competitive advantage by stealing blueprints, technical schematics, product information, intellectual property, trade secrets, employee or supplier information, financial results, performance and pricing information, future strategy or product development, etc
- Espionage (nations) to gain access to spy agency or military information, research, trade agreements, interfere in elections, damage relationships with other nations, undermine the current government, etc
- Finally, some simply find it fun or challenging, like a hobby of sorts. Being able to hack their way through a system or access content they shouldn’t be able to is a test of their skills and gives them a sense of adventure while proving themselves to their hacking friends. Whilst the motivation isn’t malicious it leads to them sharpening their skills and abilities to access more complex systems. Once they gain access to more sensitive data or content it’s not hard to imagine that they may become confident and tempted to do go further than simply the front door. Typically, these are the green-hat hackers we defined earlier but they develop into black-hat hackers over time as they gain experience and skill.
Motivations with financial benefit
To profit from their attacks here are some of the ways bad actors can monetise what they gain access to:
- Identity theft and subsequent opportunities by targeting your Personal Identifying Information (PII) it enables many forms of identity theft. With this type of information bad actors can pretend to be you and open credit cards or bank accounts to commit various frauds in your name. They can also access your various accounts through password reset procedures and cause you nonfinancial harm, such as reputational damage in the process. Finally, through identity theft they can gain access to your sensitive information, such as private photographs or medical records and hold you for ransom with a threat of exposing them publicly. This is particularly risky for those who rely on a clean public image for their career – aspiring politicians, real estate agents, business consultants, CEOs of large companies, etc
- Blackmail / ransom is similar to what’s above, but the bad actor doesn’t really exploit the PII they gain access to. Instead, when they gain access to your data, they will either encrypt it or steal it (remove it) and request a ransom to give it back. Since they’re not exploiting your PII for various frauds and scams, the ransom or blackmail will typically be of a higher value to make it worth their while. When you pay the ransom, the bad actor usually (but not always) complies by giving you the data back or providing you with the encryption key. The final way this approach differs to the point above is the bad actor actively seeks out communicating with you which is necessary to their success. With the identity theft and subsequent scams and frauds, they don’t want to draw your attention to it to ensure they have maximum time to exploit and profit before you notice and take action
- Sell on the Dark Web is the final main way a bad actor can profit from breaching your systems and accessing your data. If you’re not sure what the Dark Web is, you can read our recent article about it here. For the bad actor this is the safest approach as a third party, rather than the victim, is funding their success. However, for this reason it’s also has the lowest financial value as some time has passed and some data may not be valid or usable by the time they sell it (credit cards could already be expired or cancelled for example).
Next, we’ll look at the main types of data that are of interest and most valuable which enable bad actors to meet their financial or non-financial motives.
Part two
The types of data targeted by bad actors
This list isn’t exhaustive of course but accounts for the majority of what bad actors are looking for, value, or can profit from relatively quickly. This means as you read through the list you should be thinking about ways to secure and guard it. The types of data of value includes:
- Basic Personal Identifying Information (PII) such as date of birth, full name, phone number, and residential address – basically the standard information that identifies you to companies or that you need to complete an online transaction with
- Other PII such as social security numbers, credit card or bank account details, government issued identification such as passport or driver’s licence, etc
- Usernames and passwords to online accounts
- Financial statements or insurance policies
- Health or healthcare records (typically used to make fraudulent insurance claims or buy prescription medication)
- Private or sensitive information they could hold over you for ransom or blackmail such as explicit photographs, medical conditions, evidence of extramarital affair, tax fraud, etc
- Information on your current contacts to impersonate you in order to scam them (usually through phishing)
- Your calendar to identify your patterns of regular movements (typically for offline crimes such as knowing when you’re alone to hold you up or when no one is home for a burglary)
- Other similar types of data or content which can be used or used with other data to cause you some kind of harm (as outlined in part four below).
The typical locations they find this data include:
- As stored by companies you do business with
- Within your accounts they gain access to such as email, banking, or social media
- The storage on your physical devices such as laptop, USB drive, or smartphone
As we discussed in Challenging the way you think about imagine data it’s the volume of data that makes it powerful, not any specific individual type of data. This is where the issue of reusing the same password comes back to bite you, the table below is a quick example of what can be gained if you use the same password for just a handful of popular accounts and it gets breached.
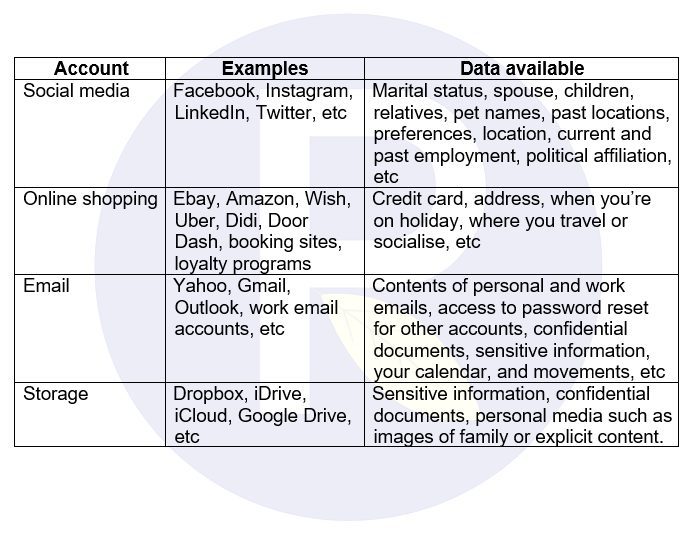
Imagine if you use the same password only six times – 2 x social media, 2, x online shopping, 1 x email, and 1 x storage. This one password holds access to all the data types listed in the table and likely more, not to mention it could be used to access other accounts via password reset procedures.
Part three
The methods typically used by bad actors
We’ve discussed the motivations of bad actors and the data types they target, let’s now turn our attention to their methods.
- Phishing scams: We’ve written about this method already in our article linked here, but in summary a bad actor will send an email or SMS impersonating a legitimate company. The message typically has urgency to it saying that time is of the essence, and you have to act immediately so as to not give you time to reflect on the issue and become suspicious. The instructions usually require you to log in to an account (usually a bank or email account) however the linked login page is an impersonation of the legitimate one and with your compliance the bad actor gains your login credentials. Deepfakes are also an emerging threat which utilise the same trickery as phishing scams to deceive people by impersonating a trustworthy source (usually people)
- Ransomware: Ransomware is a type of malware which encrypts the victim’s files, and the bad actor demands a ransom from the victim in exchange for the encryption key to get their data back. It’s usually distributed through a phishing scam but designed to mimic a trustworthy attachment or file type (rather than a legitimate website as outlined above). It can also be distributed via compromised credentials, if a bad actor can remotely log in to your device or system, they can infect it directly without you knowing. This is why setting strong passwords which you don’t reuse is so important.
Another major source of ransomware infection is from being downloaded through malicious websites or USB devices. Some bad actors go so far as leaving infected USB devices laying around public transport stops or carparks hoping that whoever picks one up is curious enough to see what’s on them and plugs it into their computer or laptop. Bad actors are going as far as tampering with the USB connection of a keyboard or mouse so even hardware with no storage capability isn’t safe.
As for the malicious websites, one way is for bad actors to purchase legitimate advertising space online and have it link to a download of their ransomware. These types of attacks are called ‘bait & switch attacks’ as they fool users into visiting a legitimate website which can have malware just one click away - Other Malware: There are other types of malware we’ve outlined previously such as keyloggers, viruses, and trojans amongst others. Read our article on malware linked here for more details on these other threats
- Brute force attacks: A bad actor tries a very large list of possible passwords to try guess the right one. Using dedicated software they can make an incredible 100,000,000 guesses every second – a six letter password can be cracked in as little as 5 seconds!
- Fake Wireless Access Point: Bad actors will impersonate a popular wireless access point with their own wireless router. They will do this in Wi-Fi hotspots which traditionally have numerous Wi-Fi networks and name it appropriately such as ‘LAX Airport Free Wifi Fast’ or similar. Once you connect to the fake access point the bad actor will have access to the data stored on the device you access from and potentially the accounts you log into whilst connected
- Missing security patches: Bad actors will exploit known vulnerabilities in existing software and attack those who ignore regular software updates
- Attack third party systems: There are a few methods bad actors can get your data indirectly by targeting a company you do business with or have an account with directly. In this scenario you’re collateral damage as you may have taken all the precautions on your own devices but are let down by those of a third party. The most popular include Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks, SQL Injections, and Cross Site Scripting.
There are other methods we haven’t detailed here in the interest of space, feel free to search some of these if you’re interested in how they work and their threat to you:
- Cookie theft and session hijacking
- IoT specific attacks
- Clickjacking
- Man-in-the-middle attack
- DNS spoofing
- Browser locking
Part four
The consequences of their success
Most people reading through to this point can already guess some of the consequences that come with being a victim of a cybersecurity breach by a bad actor. However, it’s important to see the full picture so we’ve started with the two most obvious consequences and followed it through to the lesser considered ones.
- Financial loss from paying a ransom, theft of funds from your bank account, and more long-term costs such as a ruined credit rating. If you’re the owner of a business who has been a victim you may face legal action, lost sales, fines, cost of paying a ransom, and compensation costs as well
- Reputational damage including loss of employment opportunities or ability to gain new business or clients as well as the loss of trust and credibility with existing ones. This is most common when you’re targeted specifically, and the other party isn’t interested in financial gain. As a business owner the future viability of your business would take a hit and you may be faced with additional regulatory audits by government agencies
- Family breakdown as a result of high-volume financial loss, public embarrassment, the public disclosure of private matters, or your deceit such as an extramarital affair
- Loss of personal content such as never getting back family photos or similar media which may hold sentimental value to you
- Mental toll associated with being a victim of blackmail, ransom, or fraud including the stress of your private files being accessed by someone else and potentially distributed publicly over the internet
- Psychological toll which can have both short-term and long-term impacts on the victim. A victim may become less trusting and more suspicious making them an overprotective parent or overbearing partner as a result. Some victims can also become extremely private and reclusive for the rest of their lives and avoid using technology altogether. Building trusting relationships becomes difficult for victims and can lead to the development of anxiety, paranoia, depression, and PTSD over time
- Death is the worst consequence and a very real one, victims of cybercrime have been known to take their lives.
For most of the points listed above there are also second order effects to consider when it comes to restoring everything back to its original state before the breach. For example:
- Personal: the time to restore your credit rating
- Personal: the time and dedication to repair broken relationships with family, friends, and potentially co-workers
- Personal: the time and cost of ongoing treatment and/or medication for any psychological impacts suffered
- Business: the time, cost, and dedication to restore your reputation and trust amongst customers, colleagues, and suppliers
- Business: the time and cost to clean and restore your website and other digital assets which form part of your operation (if you transact there)
- Business: the potential loss of staff from a reduction in trade or through resignation as they may feel the business may not recover
- Business: the ongoing disruptions to society with the inability to provide their product or service such as the Colonial Pipeline Cyberattack in May of 2021 which caused ongoing fuel shortages in the United States. Colonial paid the ransom of approx. $5 million (USD) via Bitcoin quickly however their network and supply took many days to return to normal. Society was struck with record high fuel prices, disruption to supply chains, disruption to mobility, fuel hoarding, large lines to fuel stations, and the stress associated with all of this across the general population.
It’s definitely time to move on and find out what we can do about it!
Part five
The precautions you can take
The following precautions speak specifically to what bad actors target as listed in this article. Obviously, a more complete approach involves being as private and secure as possible which would include other precautions not listed here.
Don’t forget you’re dealing with bad actors, complying with all instructions and paying the ransom with cryptocurrency still doesn’t guarantee they hold up their end of the agreement and provide you with the encryption key to your data. This is one of those instances where prevention is much, much better than cure.
Protecting your data
- Encrypt the data stored on your devices and in the cloud
- When opening accounts only give the minimum required information to open the account. Typically, mandatory fields are marked with a little red asterisk so look out for these. This applies to online shopping too – avoid making large numbers of accounts by utilising the ‘check out as guest’ option wherever possible
- Give intentionally false information if you’re opening an account with a company that won’t send you mail correspondence, list a different street number or street name instead of your own. Note that this may not be appropriate with serious accounts such as banking or with government agencies, but rather more social / low value accounts
- Give your recovery questions intentionally false answers, for example if the question is ‘What is your mother’s maiden name?’ answer it with ‘tomato sauce’. Obviously, you will need to make a conscious effort to remember this
- Don’t appear wealthy or with a lavish lifestyle – be conscious of social media posts illustrating your lifestyle, the car you drive, holidays you go on, location of your house, etc. Your lifestyle indicates to bad actors how much you may be willing to pay as a ransom and increases your targetability
- Clean up your social media contacts regularly and don’t accept requests from people you don’t know or only just met. You don’t need that connection to a former school or work colleague you haven’t seen or spoken to in years
- Set a lock code for your devices, don’t forget opportunistic criminals physically stealing your device in the real world may have enough knowledge to exploit the contents stored on it (and not just chasing a quick resale for cash)
- Close down accounts you no longer use and ensure you request your data be deleted by the business first, then close the account formally, and only then uninstall the app or software
- Back up your files to an external source regularly but ensure it is not linked to your computer through an app. Even in the cloud backed-up data could be encrypted by the ransomware / bad actor if there is a link from your device
- Don’t save your credit card details or delivery addresses within the profiles of your various accounts, fill them out manually every time. If you have a PO Box have all deliveries go there to hide your residential address in as many instances as possible
- Use two different emails – a personal and more private one for sensitive information, communicating with family and friends, etc. The second one for online shopping, signing up or opening accounts with, etc. The idea is the first one is less exposed online and thus less vulnerable, if one was to be breached it you’d expect it to be the second one which has more data points but importantly less sensitive content
- Research the data security history of any business before opening an account with them to ensure they take cybersecurity seriously. A history of consecutive cybersecurity breaches and data theft should be a red flag and lead you to reconsider using their services
- Research the existing security standards of any business before opening an account with them. If possible, avoid those based in a five or fourteen eyes country and visit our new room on recommended providers which are highly rated in relation to this point
- Many antimalware providers have an optional feature which can be added on to your subscription which involves Dark Web scanning or similar service regarding monitoring to see if you’ve been the victim of identity theft. If your data appears on sale on the Dark Web you will be sent an alert and some instructions on what to do next
- When you sign up to apps or open new accounts you may be prompted (or will need to manually find) an option to ‘opt out’ of data collection.
Protecting your money
- Use a separate account for online payments or direct debits which is not the account or linked to the account which holds your savings or receives your wages. Ideally, it’s with a different bank so as to have different login credentials to your wages and savings account
- Delete transaction emails from your inbox once your purchase has been delivered. If you need the receipt for warranty reasons copy it into a word processing document and save it that way or print it but don’t keep hundreds of receipts stored in your inbox.
Protect access to your accounts
- Practise good password hygiene including setting strong passwords, not reusing passwords, consider using a Password Manager, and enable 2FA on all accounts with the feature
- Don’t follow links contained in emails or SMS, type them out in a new browser instead. For example, if you get an email from your bank with a link to the login page, open a browser instead and type in your bank’s website manually. It can be worth bookmarking the websites your regularly log in to as a way of eliminating the need to type address out manually all the time. The advantage of doing this is you virtually eliminate the risk of landing on a phishing page however it carries one small risk. The risk is if a bad actor has already breached your device, they may have altered your bookmarks without your knowledge.
Protect your devices
- Invest in a reputable antimalware provider for your devices and run scans once a week and after downloading something new. For the average person the cost should be in the region of AUD $50 per year and such a subscription typically covers 5 devices. Family packages are a popular option to secure more devices
- Don’t open emails and attachments from unknown senders, utilise your antimalware provider to scan email attachments
- Only download from providers you trust – typically this should be limited to your device’s native software store (such as Google Play for Android, Microsoft Store for Windows, App Store for Apple, etc)
- Ensure you keep your software up to date
- Purchase devices and hardware new – avoid second-hand products or products with tampered packaging
- Use a two-way firewall on your device – many antimalware providers will include this in their packages
Protect yourself while online
- Use a VPN
- Avoid public WiFi – use the hotspot on your phone and connect your laptop to that instead
- Secure your home router, especially if you use Wi-Fi
Other precautions and tips
- Use your online calendar wisely as it can be used to track your movements and identify regular patterns. The best advice would be to limit who can view it and to what detail, avoid including both personal and work commitments in the same calendar, avoid entering the address of a meeting or event, and unless necessary avoid naming everything with details if ‘Private Appointment’ will suffice
- Businesses can consider employing white-hat hackers as defined in part one of this article to test the vulnerability of their website, online stores, and other digital assets. Companies such as hacktrophy amongst others offer these services
- Be conscious of your privacy and security when getting into a new relationship with someone. Avoid joint accounts at least until you’re married and avoid sharing login credentials to the same account if losing access to it would be an issue
- Ensure you remove or encrypt sensitive data from a device if you are sending it away for repairs or maintenance. IT professionals don’t always have to be ethical / white-hat hackers
- Check the state of privacy and internet censorship to any country you’re planning to visit before you leave. This may impact what devices you take with you as some may ask you to decrypt your data on arrival, not let you access certain sites, and VPNs may be outlawed amongst other differing laws regarding privacy and security which you may be accustomed to at home
- Be conscious of what you share about your private life and business interests to people you’ve only just met. Weddings, parties, networking events, business conferences, and similar places are attended by bad actors searching for potential targets
- Consider engaging a company which specialises in removing your data from data broker sites. Bad actors can collect additional data about you through legitimate data brokers
- If you do become a victim of a bad actor’s malicious intents your first priority will obviously been damage control, minimising the impact, and regaining control of the situation. However, once you have the opportunity to do so try and report it to the authorities as it could help assist in identifying a new type of threat and even the person or people behind it. There are departments at state or national level in most countries that are tasked with this job and your particular experience may provide an insight they didn’t have before. Please note if you are a business, it’s likely you must report it depending on the jurisdiction you operate in or which your affected customers reside in. Please check this so as to not make a bad situation worse.
To put it simply your goal with these precautions is to:
- Protect your devices, accounts, and PII first, and
- Reduce the amount of your PII stored on the internet second
If other actions or precautions beyond those listed above service either one of those two goals than you are reducing your attractiveness and targetability to bad actors.
Conclusion
The purpose of this article was to show what bad actors are looking for and which kinds of data or content they are interested in. The hope is by showing you what they want and what techniques they typically employ to get it that you’ll become more security focused when dealing with such types of data or content.
There are two final points we’d really like to make to finish this article:
- Bad actors will do their homework before targeting you specifically as they want to be sure you have the financial means to pay a ransom or enough wealth in your accounts to make a breach worth their time and effort. This makes it all the more important to be conscious of how you present yourself online – especially on social media
- The one thing bad actors hate most is if their target has employed plenty of cybersecurity precautions that the time and effort to try bypass them all isn’t worth the potential payoff. They target people and businesses they believe are easy targets and what we regularly refer to as ‘low hanging fruit’. Don’t feel as though your cybersecurity precautions need to rival intelligence agencies with high degrees of complexity and cost. You just need to be ahead of the average person.
That’s the point of all we do and write about, we can’t guarantee if you do certain things or use certain software that you won’t fall victim to a bad actor. Indeed, some of the examples in this article showed that weaknesses in cybersecurity can be due to human nature as much as they are due to software or hardware vulnerabilities.
Our goal is to take you, our readers, supporters, and members, out of the pool of low hanging fruit and to the point where you become an unattractive target for a bad actor. There are plenty of people who don’t take privacy and security seriously or otherwise suffer from security fatigue for bad actors to target first. We want to help you and as many others not be part of that group.
This article is written in line with our Terms & Conditions and Disclaimer. As such all content is of a general nature only and is not intended as legal, financial, social or professional advice of any sort. Actions, decisions, investments or changes to device settings or personal behaviour as a result of this content is at the users own risk. Privacy Rightfully makes no guarantees of the accuracy, results or outcomes of the content and does not represent the content to be a full and complete solution to any issue discussed. Privacy Rightfully will not be held liable for any actions taken by a user/s as a result of this content. Please consider your own circumstances, conduct further research, assess all risks and engage professional advice where possible.

